Information Assurance Technical
The information infrastructure processes stores and transmits information critical to the mission and business operations of an organization. There are commonly five terms associated with the definition of information assurance.

Quality Assurance Process Is A Complex Combination Of Project Related And Technical Activities Which Verify That A Management Techniques Software Testing Pmbok
These requirements are focused on technical knowledge and are geared toward technical staff.
Information assurance technical. These measures include providing for restoration of information systems by incorporating protection detection and reaction capabilities. DoDD 8570 is now a part of a larger initiative that falls under the guidelines of DoDD 8140. Department of Defense Directive 8570 has been replaced by the DoD CIO as DoDD 8140.
Information assurance goes beyond static information to look at the information available to processes at points in time. The information infrastructure processes stores and transmits information critical to the mission and business operations of an organization. Abbreviation s and Synonym s.
Information Assurance is a quick recipe for trouble. The DoD IACs services span across 22 Technical Focus Areas each critical to the needs of the Department and mapped to one of the three corresponding primary domain areas. Information Assurance vs Information Security Information assurance is the management of information related risks including areas such as compliance business continuity privacy non-reputation data quality operational efficiency and information securityThis is a broad mission and it is common for IA teams to involve mostly high level initiatives.
DoDD 8140 provides guidance and procedures for the training certification and management of all government employees who conduct Information Assurance functions in assigned duty positions. The information assurance and security certificate is an excellent program for prospective grad students and working professionals alike. Apply to Technical Writer Early Childhood Teacher Medical Writer and more.
Information Assurance IA is the study of how to protect your information assets from destruction degradation manipulation and exploitation. The Information Assurance Technical Framework IATF document Release 31 provides technical guidance for protecting the information infrastructures of the United States US Government and industry. IAT stands for Information Assurance Technical.
Throughout this interactive program students will build upon their current knowledge of information security and assurance in addition to developing important industry skills needed to manage IT professionals within large organizations. Of information systems by incorporating protection detection and reaction capabilities. The information infrastructure processes stores and transmits information critical to the mission and business operations of an organization.
Notice that it is both proactive and reactive. This paper reviews the recent history of the Information Assurance IA movement and examines the Information Assurance Technical Framework IATF proposed by the United States Governments. NIST SP 800-70 Rev.
But also how to recover should any of those happen. It is an broad function that touches on data quality operations compliance risk management and information security. The following are common information assurance techniques and.
IAM stands for Information Assurance Management. The Information Assurance Technical Framework IATF document Release 31 provides technical guidance for protecting the information infrastructures of the United States US Government and industry. Information Assurance Technical Framework.
The Information Assurance Technical Framework IATF document Release 31 provides technical guidance for protecting the information infrastructures of the United States US Government and industry. Information assurance can be defined as measures applied so as to protect datainformation and system holding that information by ensuring the five pillars of information assurance namely CIA Authentication and Non-Repudiation. 2 NIST SP 800-70 Rev.
Information assurance IA Measures that protect and defend information and information systems by ensuring their availability integrity authentication confidentiality and non-repudiation. Information assurance can also be defined as a protection measure grown above the practice of information security and applies to data. Further it doesnt matter whether the information is in storage processing or transit.
Information Assurance Technical IAT and IA Management IAM personnel are strongly encouraged to complete DoD training available internally eg Service Schoolhouse courses DISA web-based training or external training currently supported by your Component for courses with learning objectives directly aligned to the IA baseline certifications outlined in DoD 857001-M. IA aims to maintain integrity through means such as anti-virus software on all computer system and ensuring all staff with access to know how to appropriately use their systems to minimize malware or viruses entering information systems. Defense Systems Cyber-Security and Information Systems and Homeland Defense and Security.
The IAT certification levels are achieved by passing specific exams and having certain work experiences that meet particular requirements. Information assurance is the practice of managing risks related to information. At its core Information Assurance is about ensuring that authorized users have access to authorized information at the authorized time.
Integrity involves assurance that all information systems are protected and not tampered with. Information Assurance IA refers to the steps involved in protecting information systems like computer systems and networks.

Assurance Technical Information Saica

Quality Assurance Process Quality Assurance Math Projects Software Testing
Information Assurance It Governance Usa

Guide To The Best Cybersecurity Certifications For 2021
![]()
Information Assurance It Governance Usa

Pin By Art Chi On It Solution Strategic Planning Cyber Security Security

Roles Of Three Lines Of Defense For Information Security And Governance
10 Best Cyber Security Certifications To Boost Your Career In 2021

Roles Of Three Lines Of Defense For Information Security And Governance

Centre Of Expertise Cyber Security The Hague University
What Is Information Securtiy Policy Principles Threats Imperva

The 3 Types Of Security Controls Expert Explains Purplesec

Total Information Assurance Framework For Modular Implementation Framework Awareness Modular

Business Functions Model Dragon1 Enterprise Architecture Business Competitive Analysis
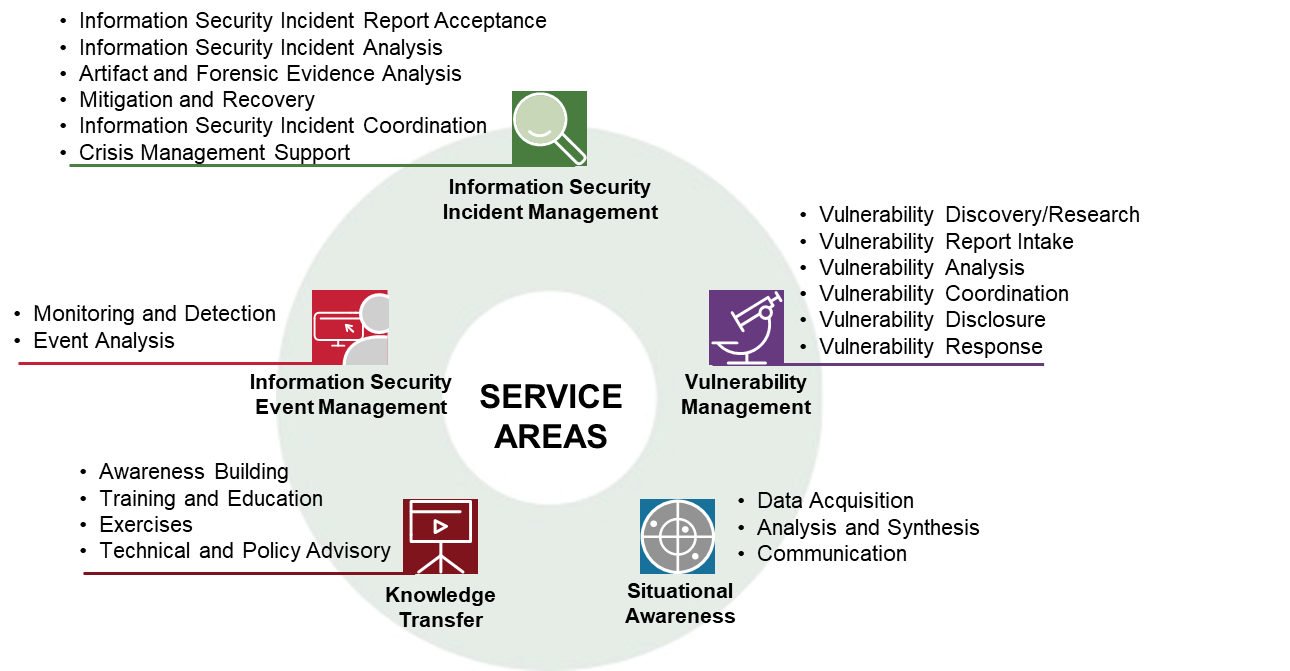
Csirt Services Framework Version 2 1

Cyber Threat Susceptibility Assessment The Mitre Corporation

Itil 4 Management Practices Bmc Software Blogs
Posting Komentar untuk "Information Assurance Technical"